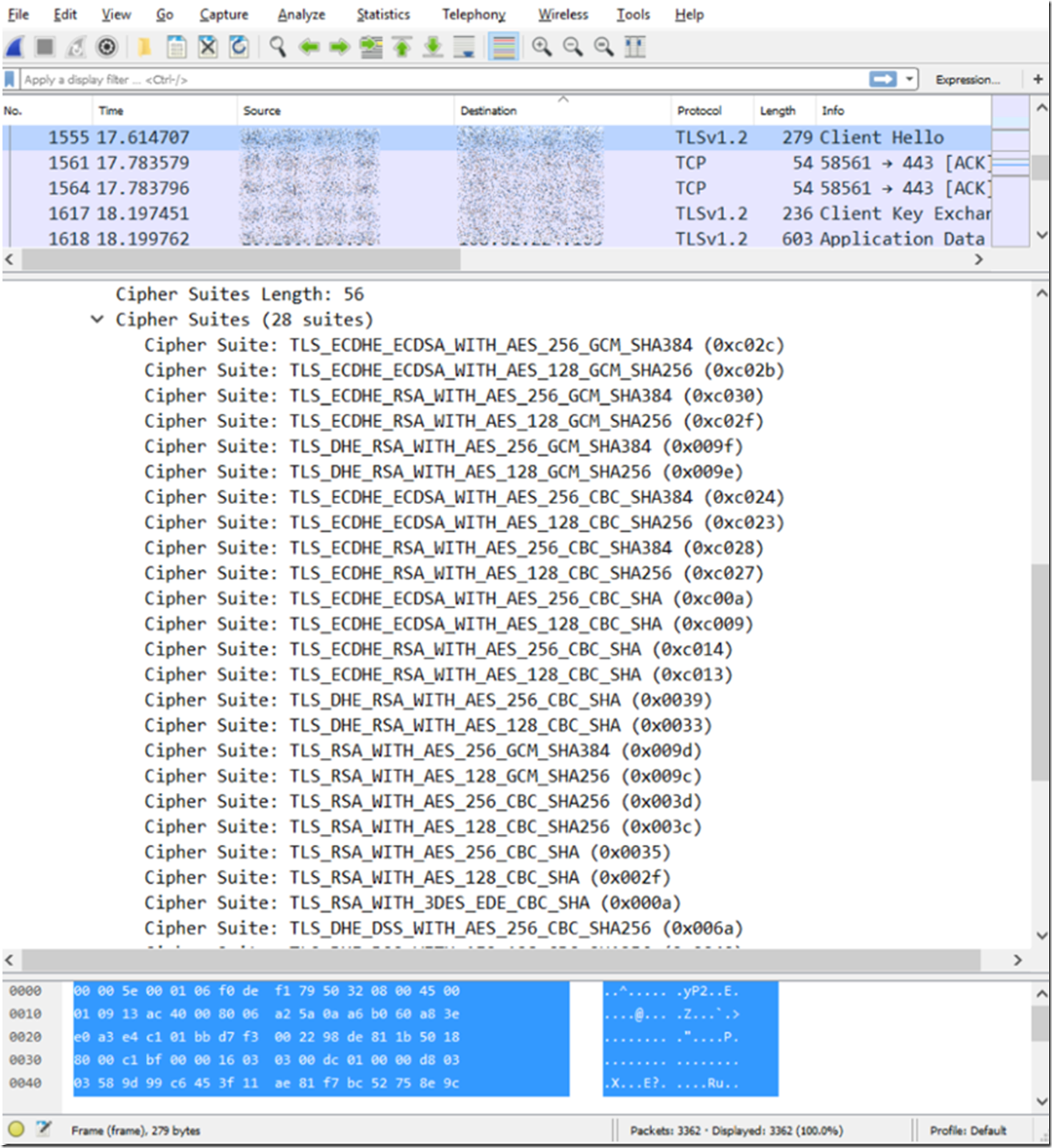
I wrote an article here about TLS 1.2 which listed out the cipher suite used to negotiate security settings (encryption) between a client and server via a Network Monitor trace. You can probably see the same using Wireshark. Regardless, here is a nice Wiki article about cipher suites.
It was a journey getting to the dumping out of this using KUDU/SCM, which I describe here. It all started when I found this PowerShell cmdlet:
Get-TlsCipherSuite
I tested this on my workstation and it did indeed listed out the cipher suites, trying the same via the KUDU/SCM console did not function. Method #1, fail. I kind of expected that one not to work because of the sandbox in which Azure App Services run, described here. And of course, it could be due to my lack of PowerShell knowledge, I am a GUI guy. NOTE: you cannot change or modify the cipher suite on the Azure App Services in any way. If your applications requires a specific order to a a cipher which is not present, then it cannot be deployed to an Azure App Service. You can consider an Azure VM or perhaps a Cloud Service with a startup script of some kind.
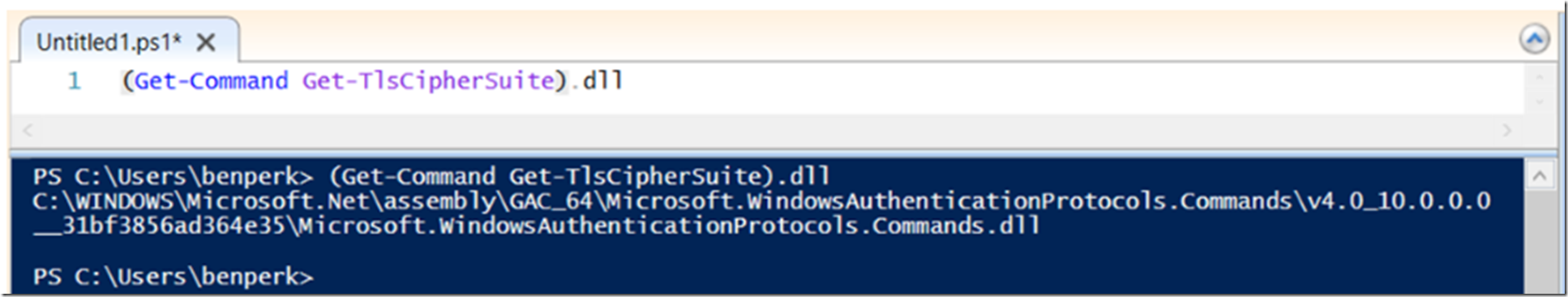
Then I recalled an announcement (here) that PowerShell was now Open Source on GitHub here so I wanted to go find out what the Get-TlsCipherSuite cmdlet was doing. I did some searching and even after executing the following command, Figure 1, that showed the module, it was apparently is not there. Method #2, fail.
(Get-Command Get-TlsCipherSuite).DLL
Figure 1, find the module of a PowerShell cmdlet
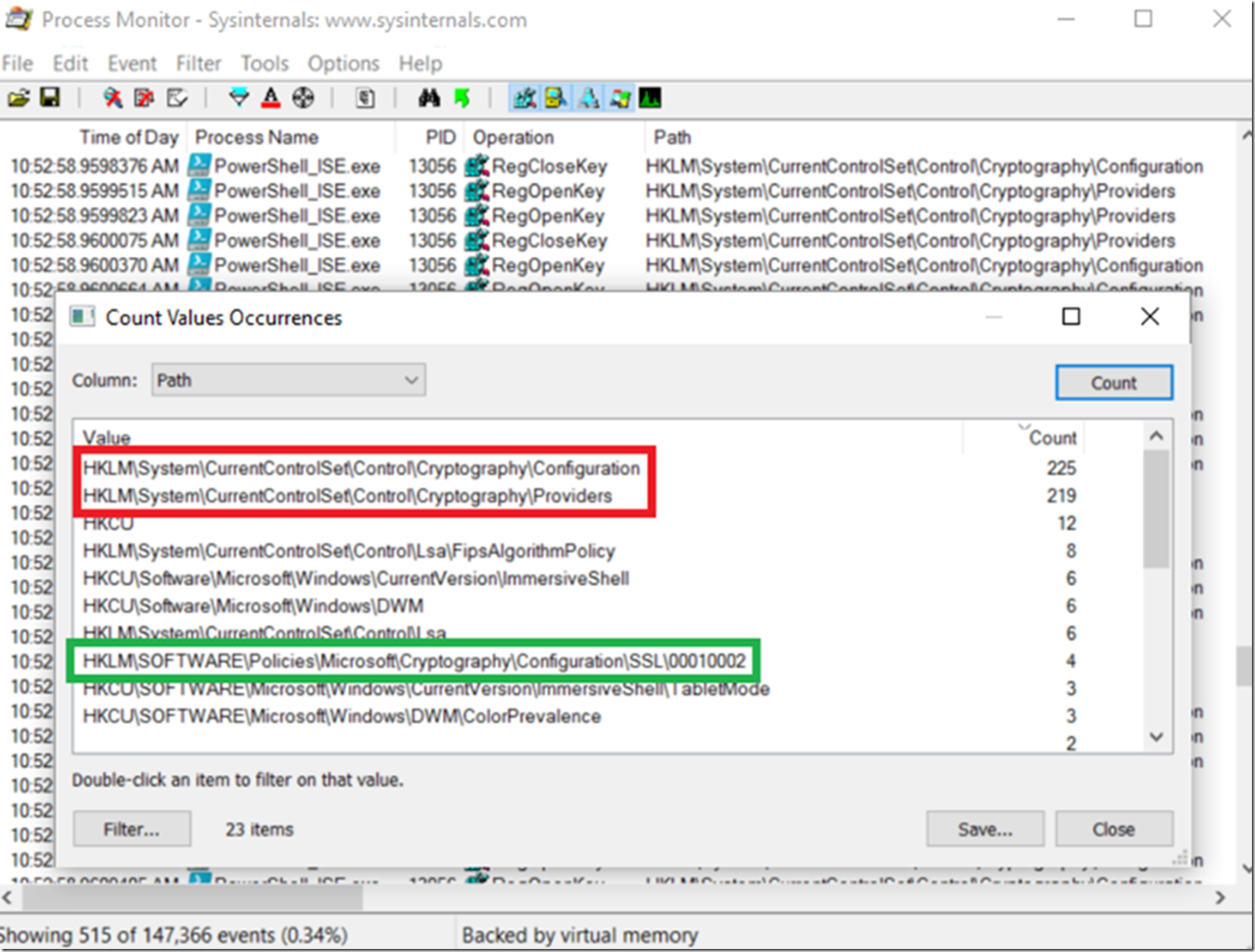
I knew that the cipher suites were written in the registry, but did not want to scan it all and maybe I would miss something, then I remembered writing this article, “Using Process Monitor to solve any problem” here. So I spun up Process Monitor and executed the Get-TlsCipherSuite cmdlet on my workstation. I found that the following registry keys were accessed the most during the execution of that cmdlet, Figure 2.
- HKLM\SYSTEM\CurrentControlSet\Control\Cryptography\Configuration
- HKLM\SYSTEM\CurrentControlSet\Control\Cryptography\Providers
Figure 2, where are the cipher suites stored in the registry
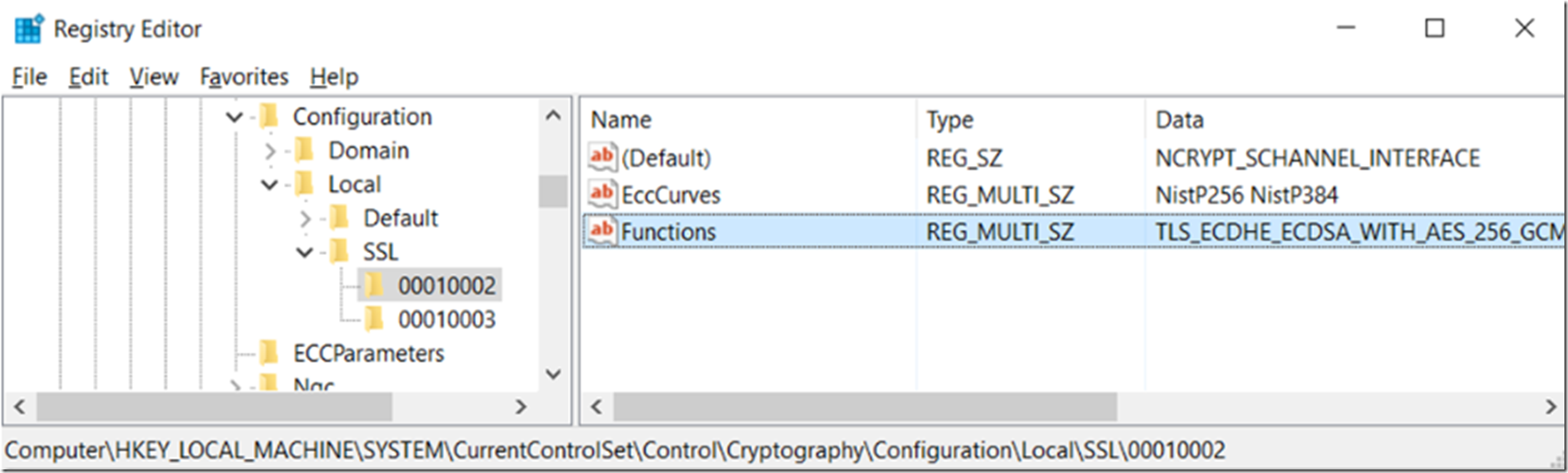
However, this wasn’t the place where I found the ciphers stored. After some snooping around, I found them in the HKLM\SYSTEM\CurrentControlSet\Control\Cryptography\Configuration\Local\SSL\00010002 folder, Figure 3.
Figure 3, where are the cipher suites stored in the registry
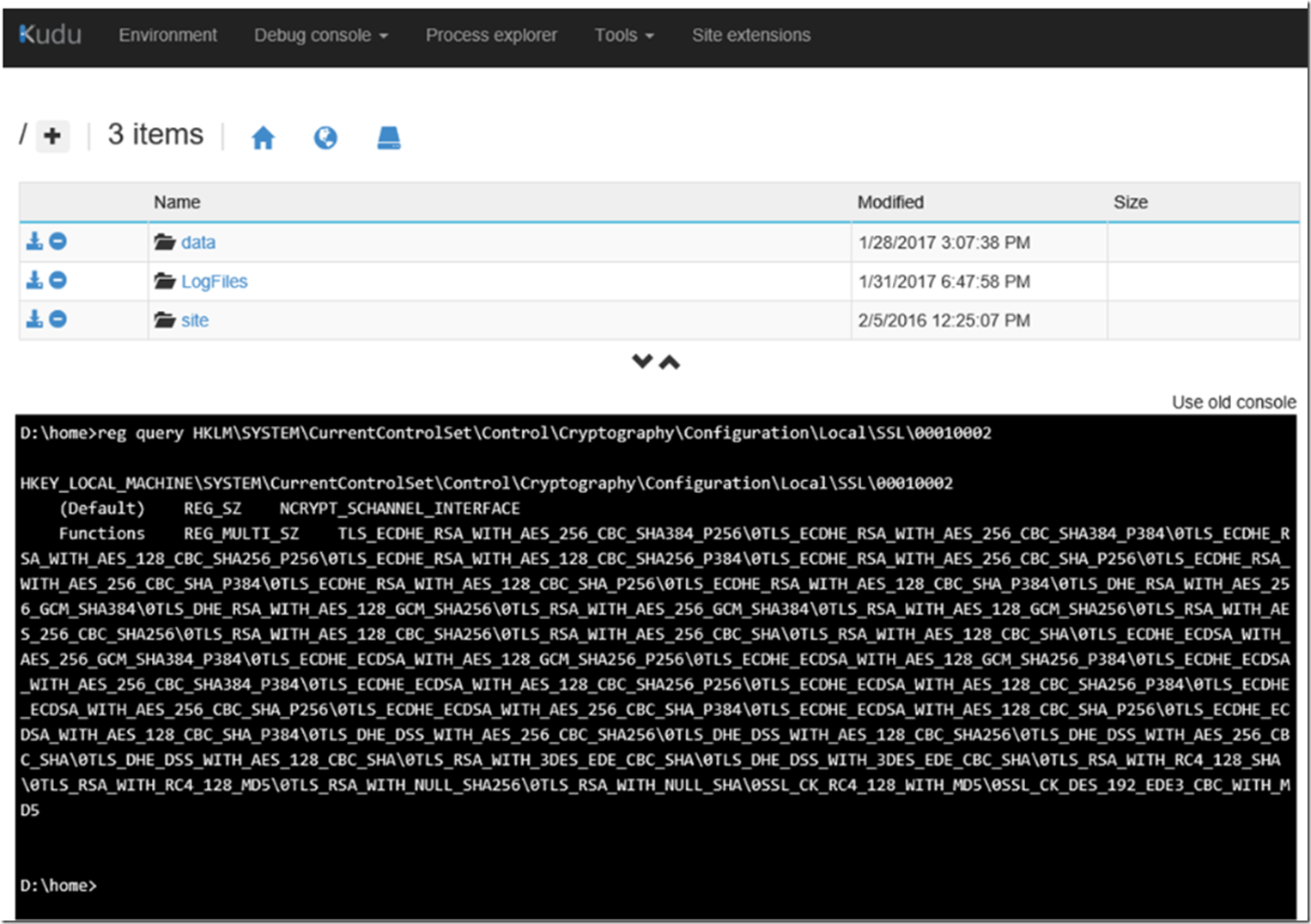
I knew it was possible to dump the values in the registry using KUDU/SCM after writing this article here (Visual C++ Redistributable Packages for Visual Studio Azure App Service), so I decided to execute a similar command via the KUDU/SCM CMD console.
reg query HKLM\SYSTEM\CurrentControlSet\Control\Cryptography\Configuration\Local\SSL\00010002
And there you have it, the cipher suites on the Azure App Service Web App, Figure 4.
Figure 4, what are the cipher suites on an Azure App Service Web App
But, you can get them with WireShark in the correct order as well, Figure 5.
Figure 5, what are the cipher suites on an Azure App Service Web App