I’m not a hacker, I don’t see the good that can come from it really. But, I do want to know how to do it so I can take necessary precautions. Also, I read about hacking and wonder sometimes if it really is possible these days. The attack vector which exploits the vulnerabilities of humans, like I’ve said before do not interest me so much. I am more interested in these two attack vector types:
- A network and/or server that has the proper security tools and hardware but are incorrectly configured or installed
- A network and/or server that has the proper security tools and hardware which are correctly configured and installed but still have a vulnerability
A good place to start is with the Kali Linux Metasploit penetration toolkit which you can get and learn about here.
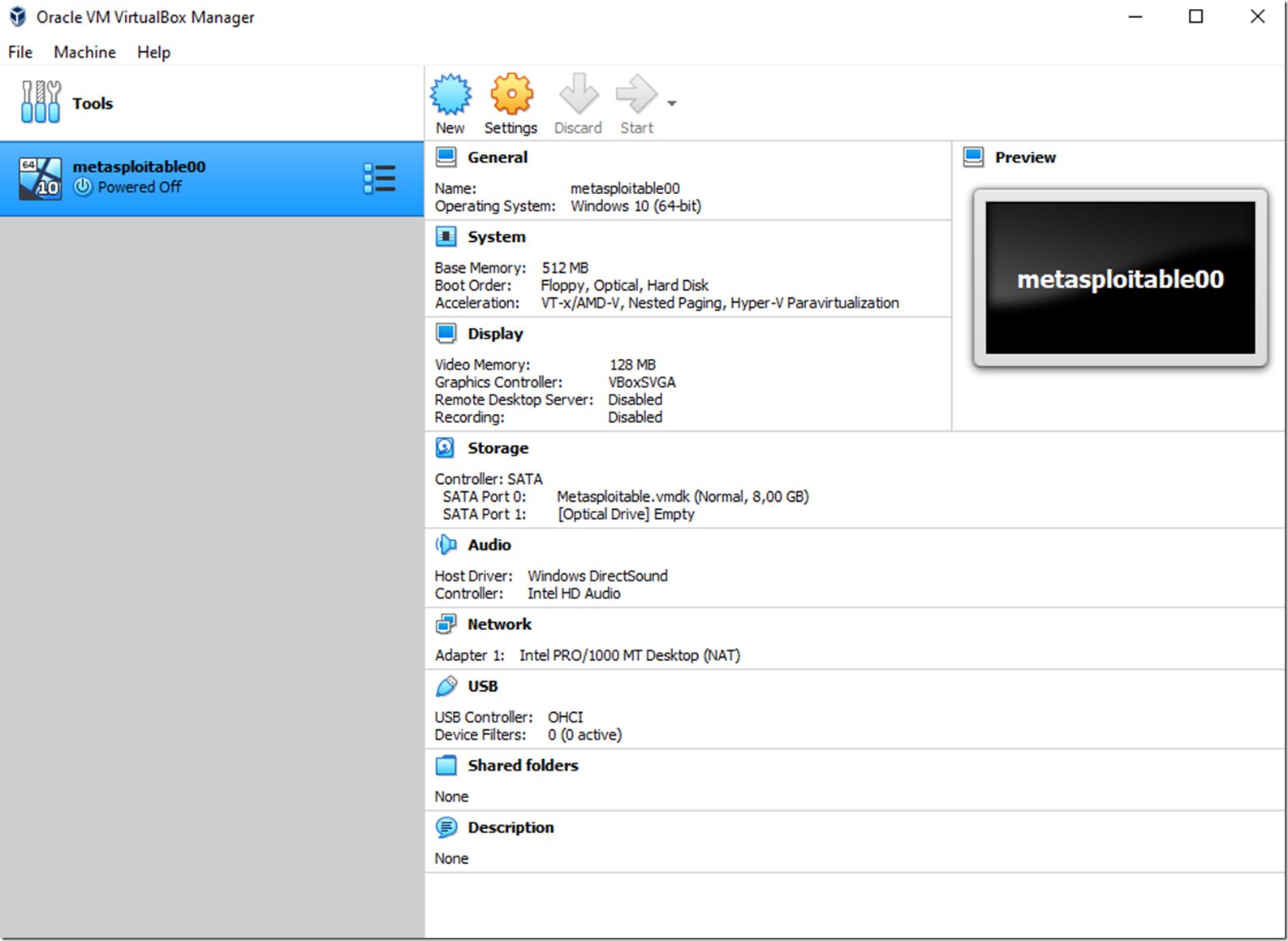
Figure 1, Kali Linux Metasploit toolkit
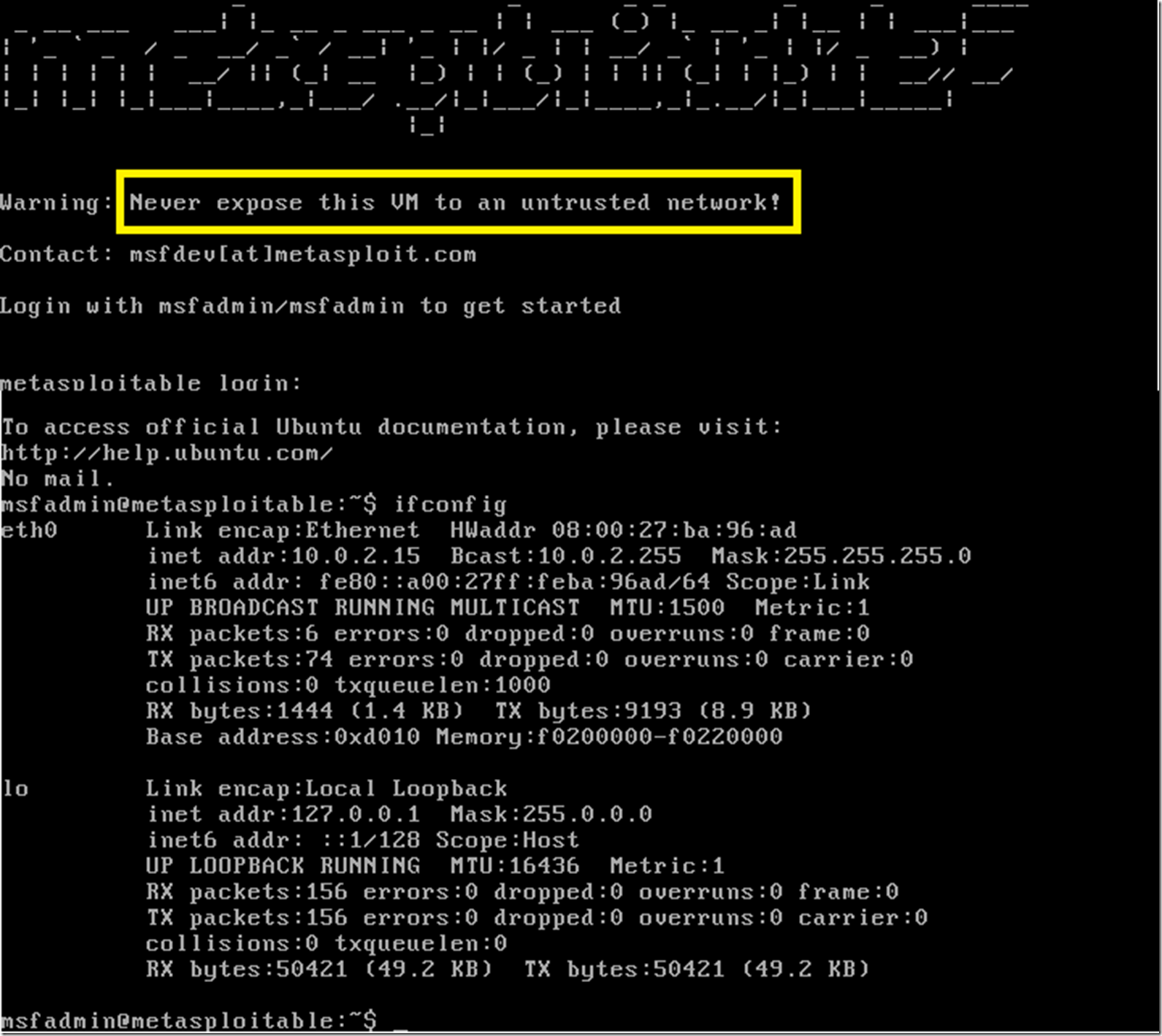
Those tools are cool, but you need something to use them on. Knowing that hacking is illegal, I read someplace that even scanning endpoints for vulnerabilities, even if you don’t exploits them has some serious consequences. I therefore have built a instance of Metasploitable which I downloaded from Rapid7. I must admit, that I wanted to use Microsoft products to make this happen, but suffered some real setbacks when I was doing it. I made it through most of them but finally met my match when trying to get the Metasploitable server to get an IP address while running in Hyper-V. Yes, I did convert the VMDK to a VHD and all. I simply wasn’t and still not so skilled with Linux to get the eth0 configuration to show an IP address. So I downloaded, installed and configured VirtualBox with the VMDK and it worked like a snap. Figure 2 shows VirtualBox and Figure 3 shows what I had been after for a few months, actually, my first attempt at this was over a year ago. I must have really wanted this, yes, indeed I did.
Figure 2, VirtualBox running Metasploitable
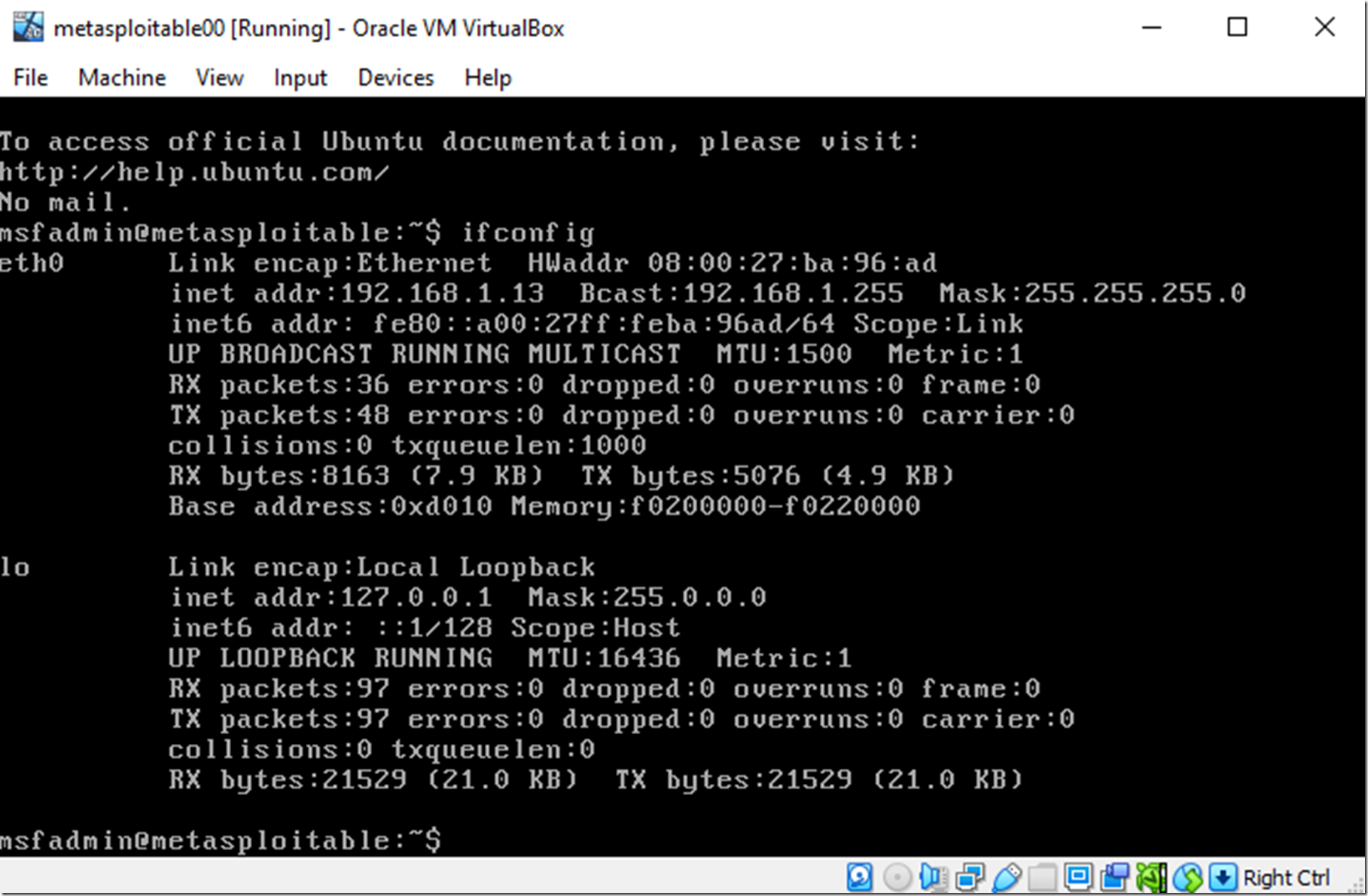
Figure 3, Metasploitable login screen and ifconfig
Note to self, I do not remember making a configuration to add Metasploitable to a different subnet than my other raspberry pi’s I am am going to use for running Kali. The pi’s were 192.168.1.2 – 192.168.1.10, somehow metasploitable00 got 10.0.2.15 like I show in Figure 3, not sure if this will cause me some more headaches, but I remain optimistic that my controller pi and Kali pi will find it when I do an NMAP. In case you are interested, I created a raspberry pi cluster which I documented here.
Just for my general recollection:
| IP Address | Role | Name | Network |
| 192.168.1.0 | Broadcast | N/A | N/A |
| 192.168.1.1 | Router | N/A | N/A |
| 192.168.1.2 | Raspberry Pi Controller | controller | Wireless |
| 192.168.1.3 | Raspberry Pi Node (SenseHat) | node00 | Wireless |
| 192.168.1.4 | Raspberry Pi Node | node01 | Wired |
| 192.168.1.5 | Raspberry Pi Node | node02 | Wired |
| 192.168.1.6 | Raspberry Pi Node | node03 | Wired |
| 192.168.1.7 | Raspberry Pi Node | node04 | Wired |
| 192.168.1.8 | Raspberry Pi Node (SenseHat) | node05 | Wired |
| 192.168.1.9 | Raspberry Pi Node (6502) | node06 | Wired |
| 192.168.1.10 | Raspberry Pi Node (Kali Linux) | node07 (kali) | Wired |
| 192.168.1.11 | Raspberry Pi Node | node08 | Wired |
| 192.168.1.12 | Windows VM host | win00 | Wired |
| 192.168.1.13 | metasploitable00 | METASPLOITABLE | Wired |
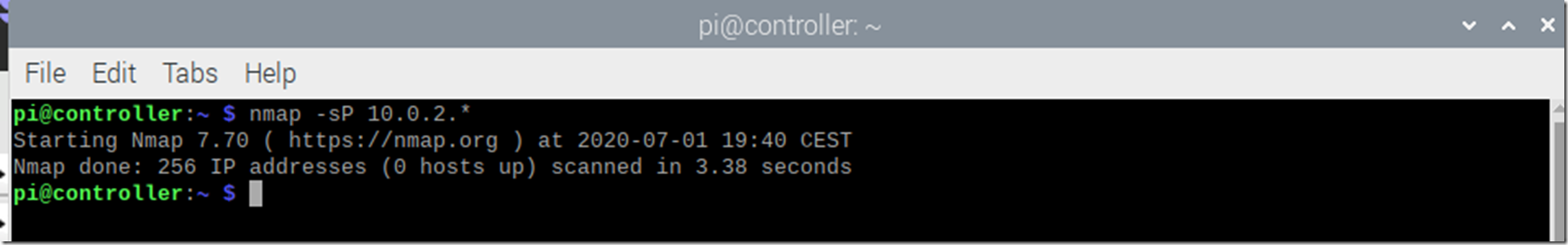
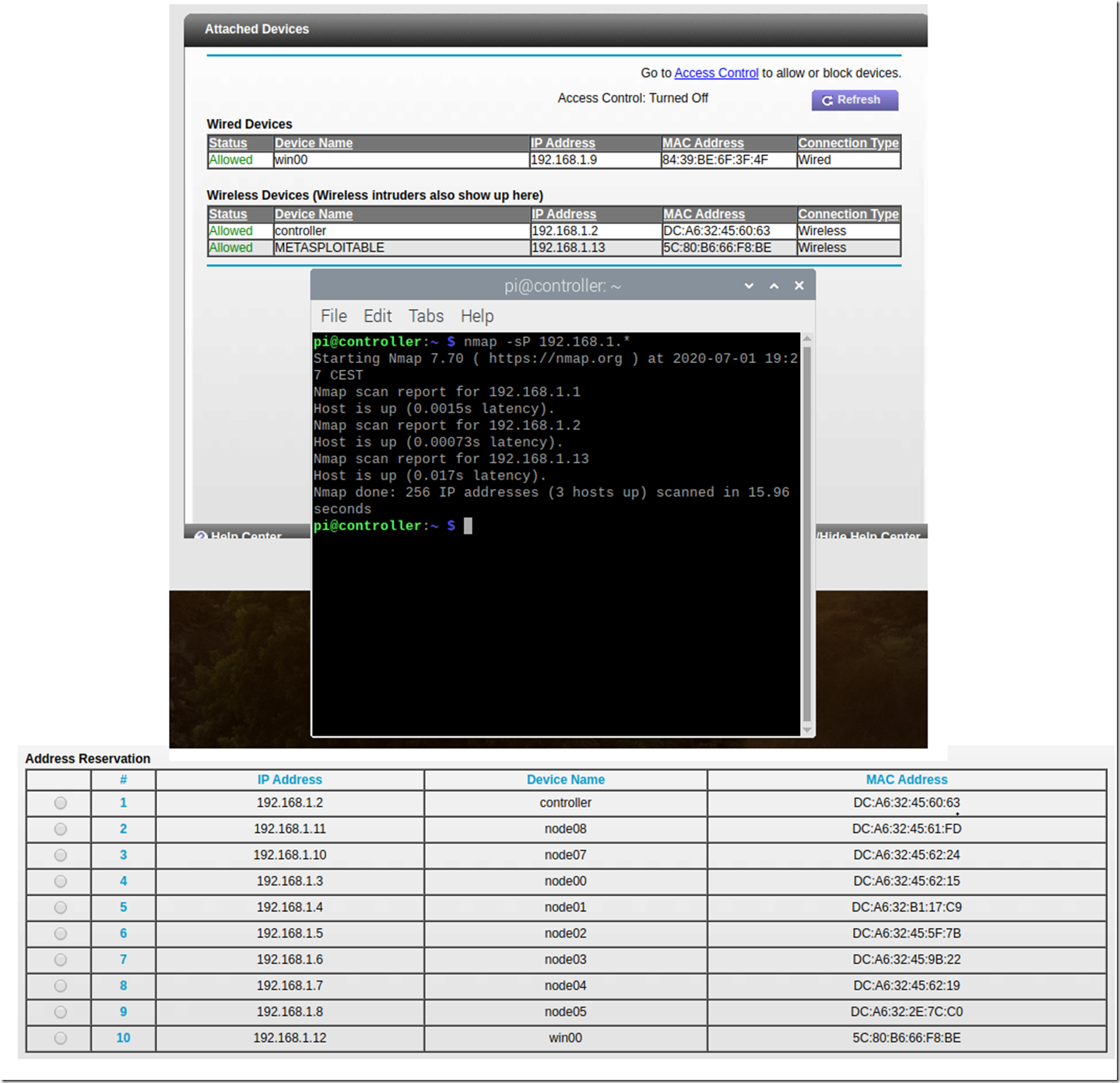
Well, it turns out that the default IP configuration for a VM running with VirtualBox is to use Network Address Translation (NAT). This is helpful and useful when I want my VM to make outbound connections (in this case I do not) and not useful when I want to access the VM from other machines on on my network (this is what I need/want to do). The default IP for this is what I quoted earlier, 10.0.2.15. As you can see in Figure 4, NMAP from my controller cannot find this one, so I will need to make some configuration and implement Bridged Networking which is apparently what I need.
Figure 4, NMAP from my raspberry pi node cluster controller
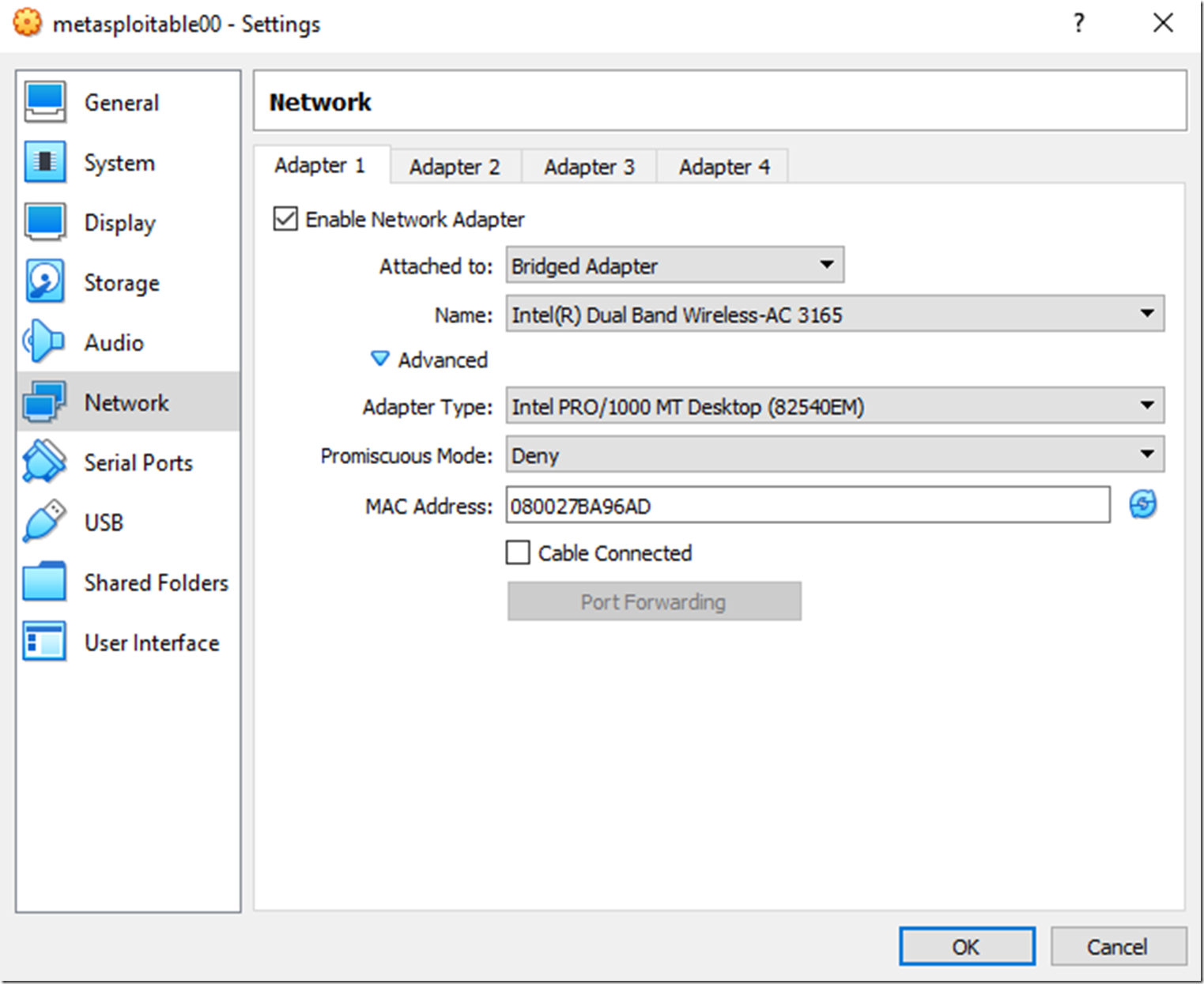
Let’s do this and hope it works out. I shutdown the VM and changed the Network settings as shown in Figure 5. My host machine is connecting to the network using wireless, you can see in Figure 5 that Cable Connection is unchecked, I assume that is what it means. Let’s press OK and see what happens.
Figure 5, setting the Network Adaptor on my VirtualBox Metasploitable VM
No go, memories of my Hyper-V trials and hardships are beginning to return to my memory. Let’s connect a cable and see if that changes anything. Finger crossed! I’m going to go ahead and shutdown the host running the VM as well before I insert the ethernet (RJ-45) cable. Nope, here we go again….wait I forgot to check that Cable Connection box. Holy smokes, let go, Figure 6 shows it got the 192.168.1.13 IP address allocated.
Figure 6, Bridged Networking configured with a Metasploitable VM using VirtualBox on Windows 10
Well, that did work and am happy about that. As you can see in Figure 7 something is a little weird with the IPs. IP address 192.168.1.12 should be the address of win00, 192.168.1.13 is a good number for METASPLOITABLE, lucky number 13. It weird because the MAC address for win00 is the one for metasploitable00 and the MAC address of win00 is the one shown for METASPLOITABLE. I’ll need to check this out and see what’s going on. 192.168.1.13 does have SSH enabled so this has to be the metasploitable00 VM because I tried the same for win00 (192.168.1.12) and it timed out because SSH is not yet enabled on that machine. I can fix this, it’s just surprising because I only know because I know, no one else would know without having set this up…
Figure 7, NMAP and Router IP configuration
If I look at the list it turns out node06 didn’t connect. Also, when I changed node00 to connect via wireless, using these instructions from wired, it got a new IP address and I needed to delete and re-add the address reservation in the router. All is good with node00 and node06 now, both have a static / reserved IP address. When I swap out the OS image on node07 where I will run the Metasploit toolkit with Kali Linux I get the same IP address as I got when it was running the Raspbian OS, this kind of confirms that the IP allocation is based on MAC Address, which I suspected before and now believe to be most probably true.
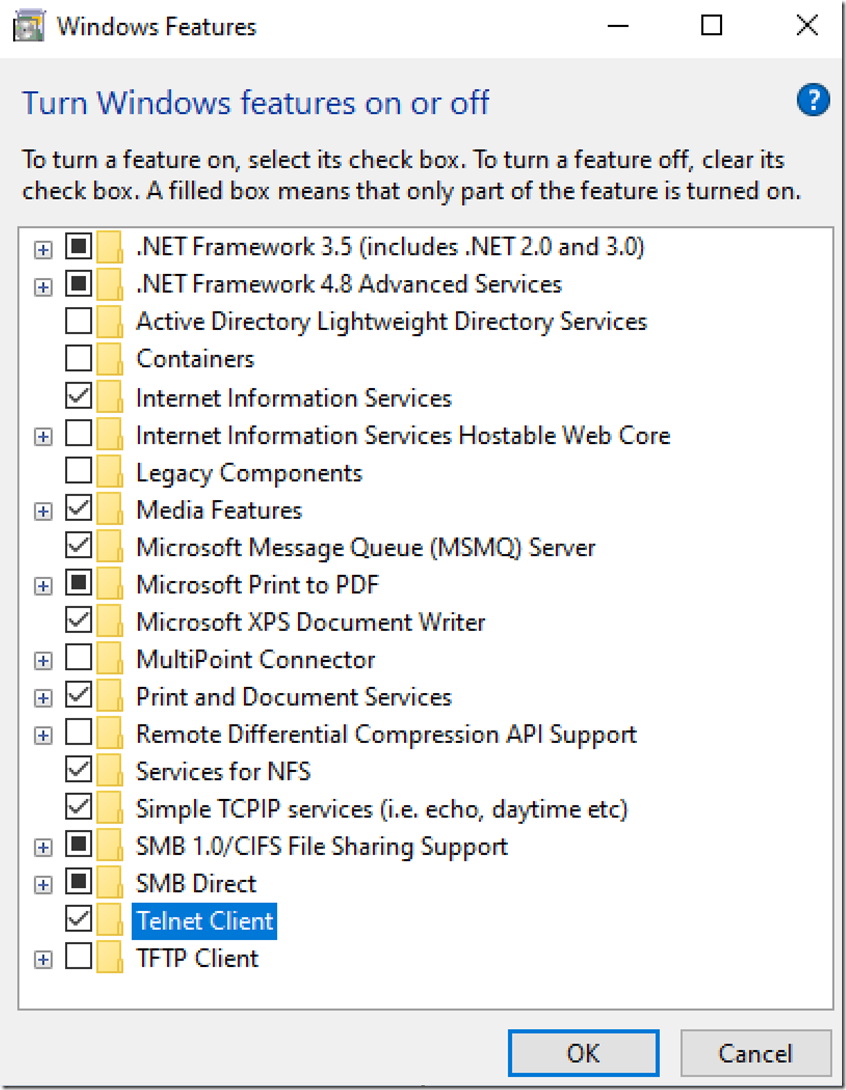
I enabled SSH, IIS and SMB 1.0 on win00 since I might want to do some hacking of the Windows 10 host at some point in the future. I used the Windows Feature from the Control Panel to install those drivers and programs, as seen in Figure 8.
Figure 8, Installing some protocols that expose a network endpoint for future hacking opportunities
I can’t figure out the IP address allocation logic with win00 and METASPLOITABLE. There is one IP address 192.168.1.12 which is linked to the “Wireless LAN adapter Wi-Fi” configuration when I look at the ipconfig. While 192.168.1.13 is the “Ethernet adapter Ethernet”. METASPLOITABLE is allocated 192.168.1.14 and I was able to SSH to it from y controller, I haven’t tried from Kali yet, but will do it first thing when I’m ready to doing some labs. I feel like the infrastructure is setup now and once I get some time I can start getting to it.
Some helpful Linux commands:
ifconfig
ssh userid@192.168.1.?
sudo shutdown –h now
sudo reboot –h now
pi/raspberry
kali/kali
METASPLOITABLE/kali